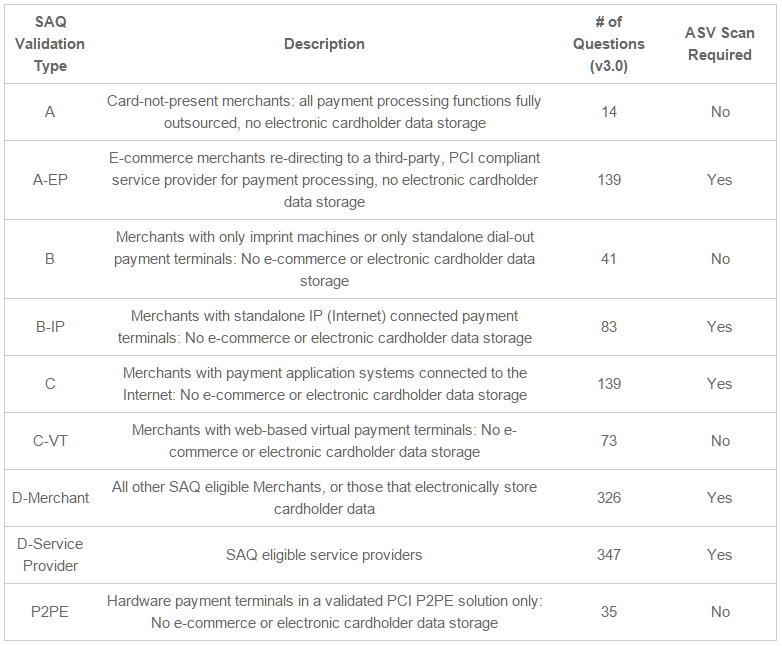
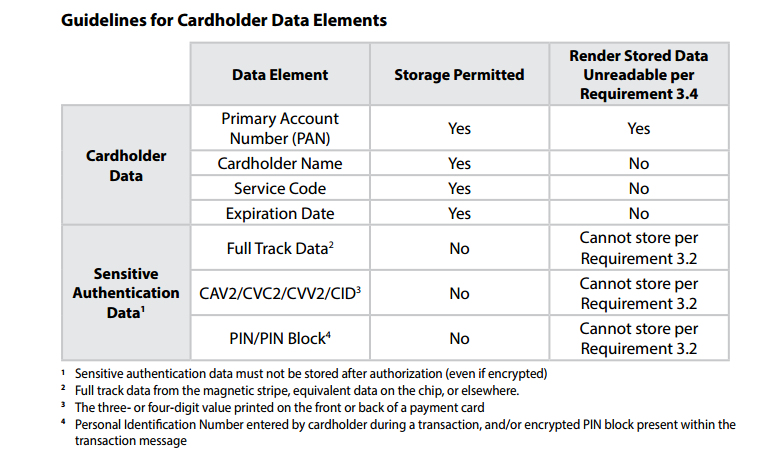
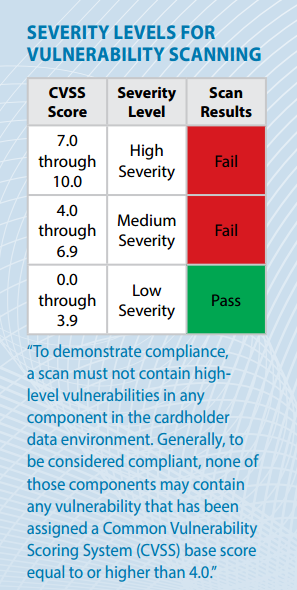
Firewalls are devices that control computer traffic allowed in and out of an organization’s network, along with sensitive areas in its internal network. Firewalls can also appear in other system components.
All your networking devices that transmit or receive cardholder details should be tested. The steps to do so are as follows.
1. Establish and implement firewall and router configuration standards that:
- Formalize testing whenever configurations change
- Identify all connections between the cardholder data environment and other networks (including wireless) with documentation and diagrams
- Document business justification and various technical settings for each implementation
- Diagram all cardholder data flows across systems and networks
- Stipulate a review of configuration rule sets at least every six months
2. Build firewall and router configurations that restrict all traffic, inbound and outbound, from “untrusted” networks (including wireless) and hosts, and specifically deny all other traffic except for protocols necessary for the cardholder data environment.
3. Prohibit direct public access between the Internet and any system component in the cardholder data environment.
4. Install personal firewall software on any mobile and/or employee-owned devices that connect to the Internet when outside the network, and which are also used to access the network.
An approved method for installing PCI-compliant firewalls is available below.