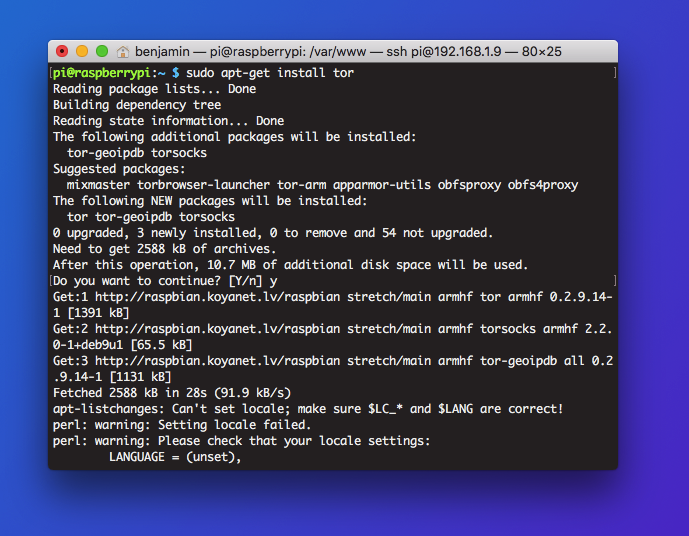
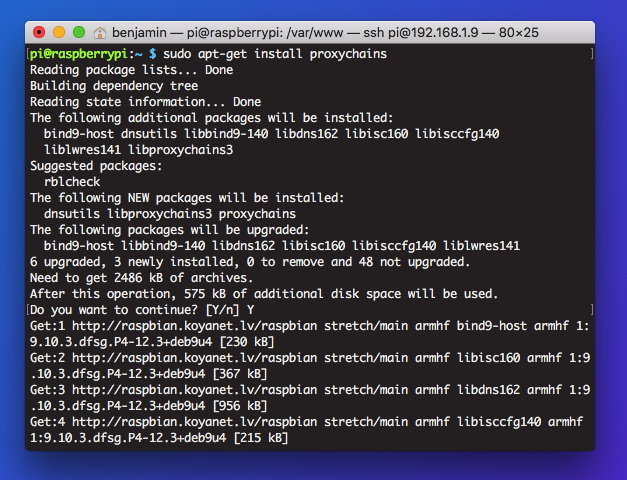
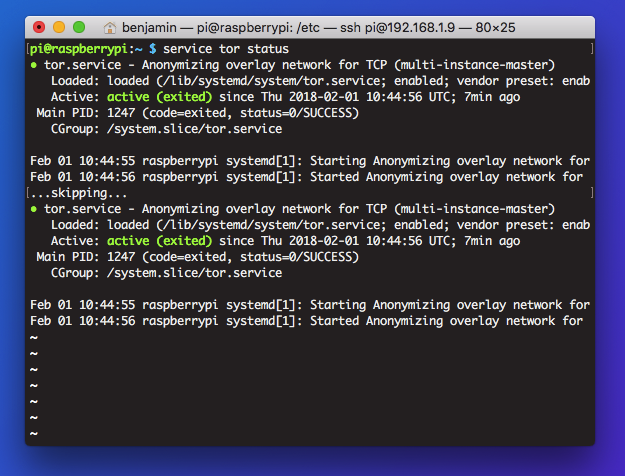
In business, proxy servers are often used in penetration testing to simulate attacks on networks without leaving a trace. Here, we're going to set up a proxy server using ProxyChains.
ProxyChains is a powerful open source tool for passing infiltrating traffic through a number of proxies, making it difficult to attribute traffic to its source because it chains a number of proxies together and rotates traffic through each. It's a tool that has seen years of widespread adoption and trust in the community.
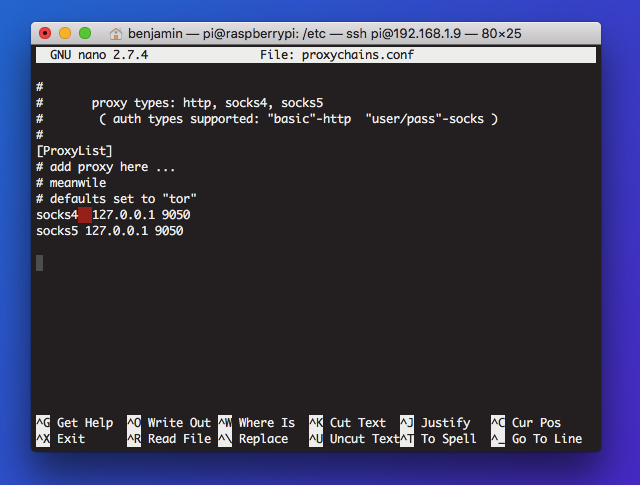
Setup is simple, and the configuration file comes with smart defaults and helpful comments.