This Process Street firewall audit checklist is engineered to provide a step by step walkthrough of how to check your firewall is as secure as it can be.
We recommend utilizing this firewall audit checklist along with the other IT security processes as part of a continuous security review within your organization, provided you are able to do so with the resources you have.
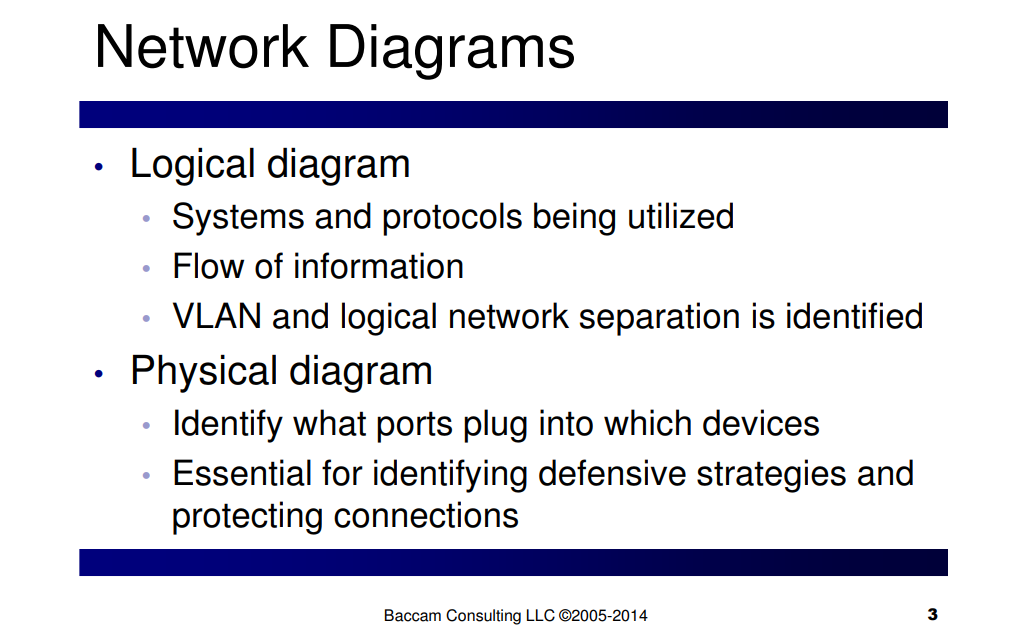
This checklist searches for vulnerabilities in your security defenses and also serves as a maintenance tool to habitually clear away clutter and update your restrictions and permissions for relevancy.
This template is entirely editable and allows you to add and remove tasks while also editing the content inside them. This means you can tweak this checklist to fit the exact needs of your organization.
Throughout the template, you will see form fields where data can be entered. Any information inputted into the form fields is then stored in the template overview tab for further reference, which you can also download as a CSV file if you want to store your own logs.
If you want more information on firewalls, watch the video below: