A massive 61% of companies have experienced critical incidents in the last two years — that includes data breaches, unauthorized access, and denial of service attacks.
Are you in this wide majority of organization?
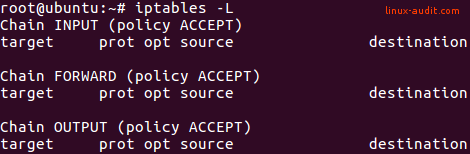
Do you have a formal incident response plan?
Most organizations (91%) do not believe their incident response processes are very effective, which indicates a need for a standardized checklist that is built out and developed with help of the whole information security team.
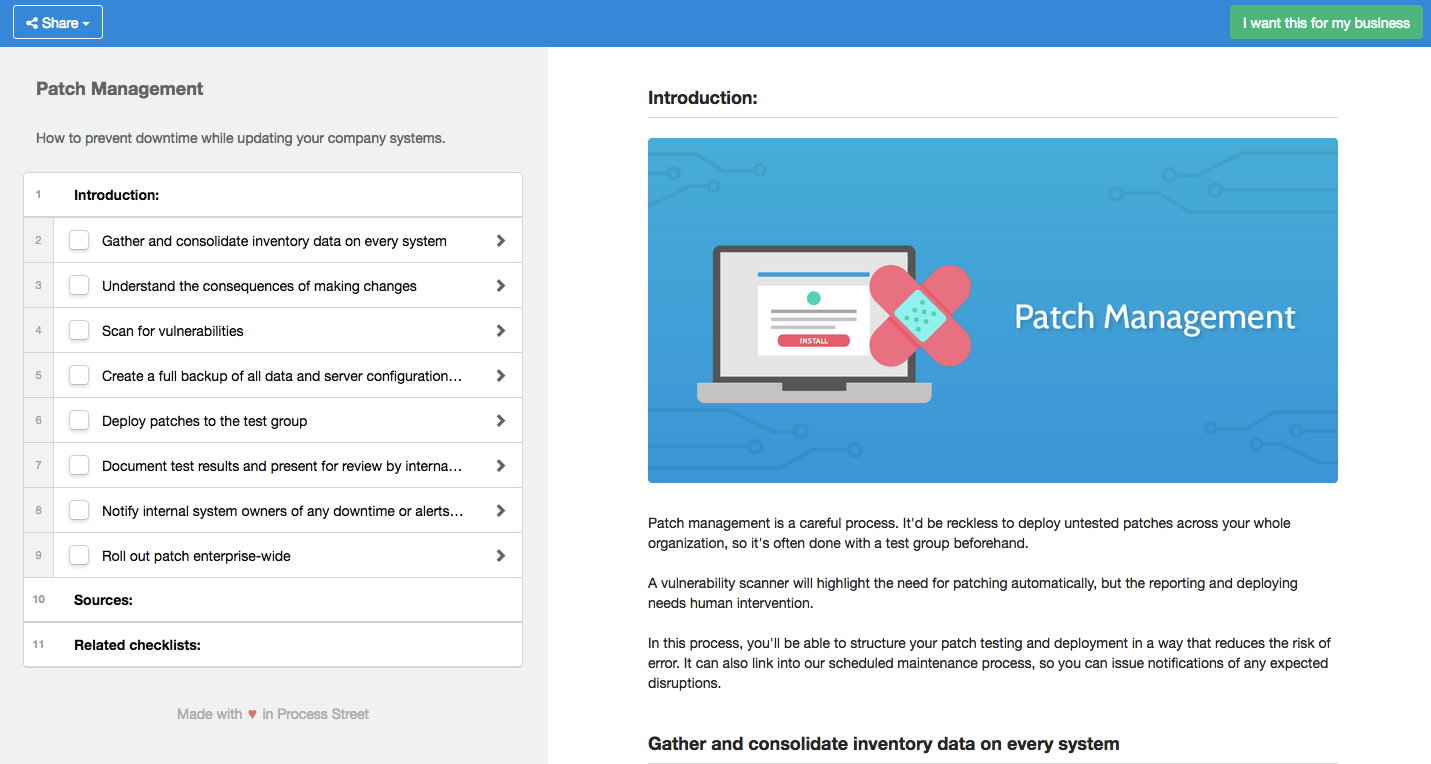
This checklist serves as a starting point, and will demonstrate the general procedures that should be taken into account.
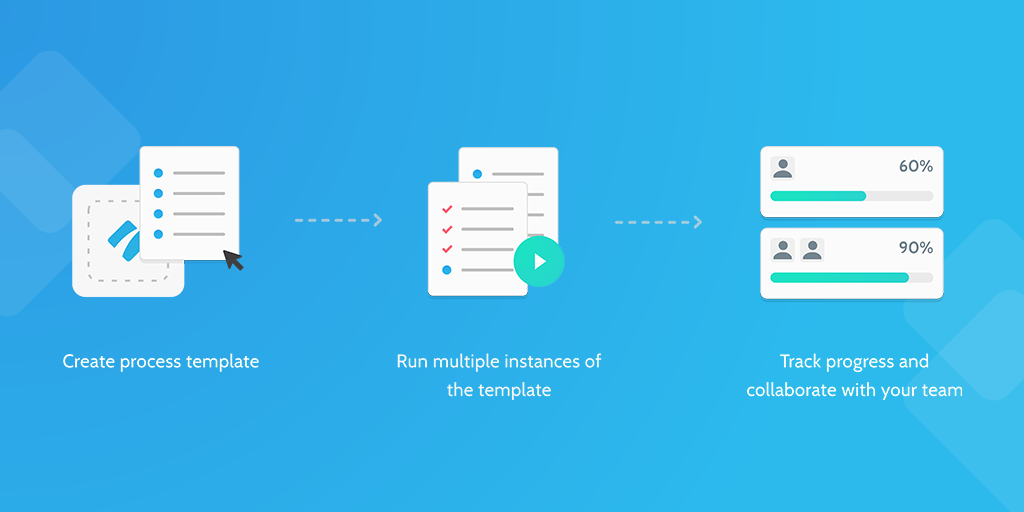
For a full explanation of how to set this checklist up, including handy conditional logic and features that you only get when you use this checklist in your Process Street account, make sure to refer to this checklist's blog post counterpart.