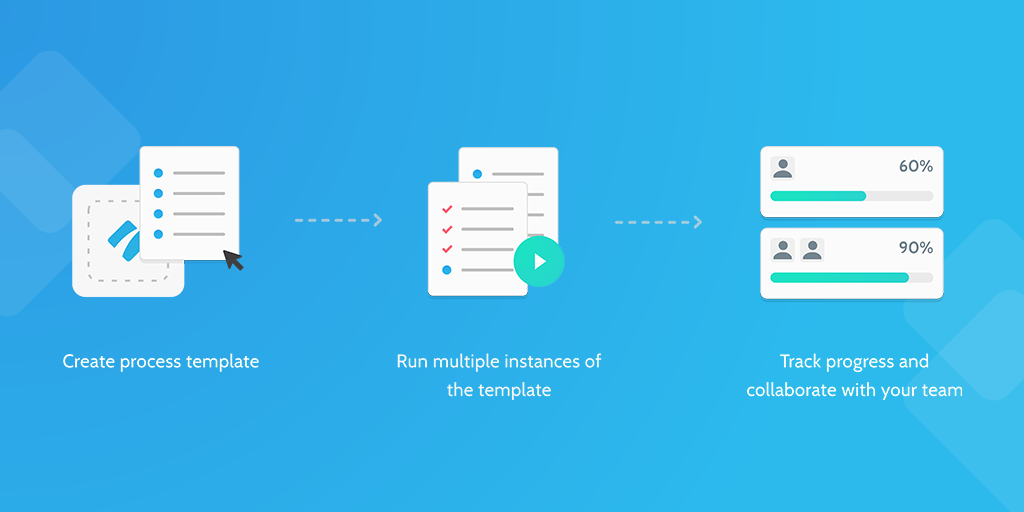
Network security management can be one of the most imposing tasks to set your mind to; how exactly do you go about ensuring the functionality, security and general health of an entire network?
"Over 70% of organisations report having been compromised by a successful cyber attack in the last 12 months" - David Shephard at NetIQ
Not only does the task cover a huge base of potential entry points for the aspiring hacker, but the field on which your battles are fought is constantly changing.
Routine system updates can sometimes prove just as dangerous as dubious software installs from unverified vendors, and given enough time, vulnerabilities in your system security will be uncovered.
However, by running this network security management checklist regularly (we recommend once every fortnight), you can protect your system and prepare for the worst.
From locking down potential access points to backing up important data, read on to cover your network with the security it needs.