The following is a guest post submission from Nathan Sykes. Nathan is the founder of Finding an Outlet, a site dedicated to the latest in B2B IT news and trends. Follow him on Twitter @nathansykestech to read his latest articles.

As cloud-based solutions, like SaaS and remote technologies, become more prevalent than ever we’re starting to see regulators and auditors get more serious about IT governance standards. As standards become more stringent, companies become more aware of the requirements set upon them and, in turn, ask providers to help with IT audits.
As you might expect, this means the pressure gets offloaded onto SaaS providers, who don’t generally perform audits or mind regulatory requirements outside of their own responsibilities. But the landscape is changing rapidly, not just in regards to audits but additional regulatory and legal constraints too, right along with financial limitations and tax requirements.
What exactly is changing in the SaaS legal landscape, and what do you need to know about it?
Sales tax and nexus
In October 2017, the U.S. Supreme Court ruled in South Dakota v. Wayfair that internet-based and e-commerce retailers can be required, by law, to pay and collect sales tax in states even where they lack a physical presence. This completely uproots decades of legal precedence, not the least of which relates to the concept of nexus.
How nexus applies
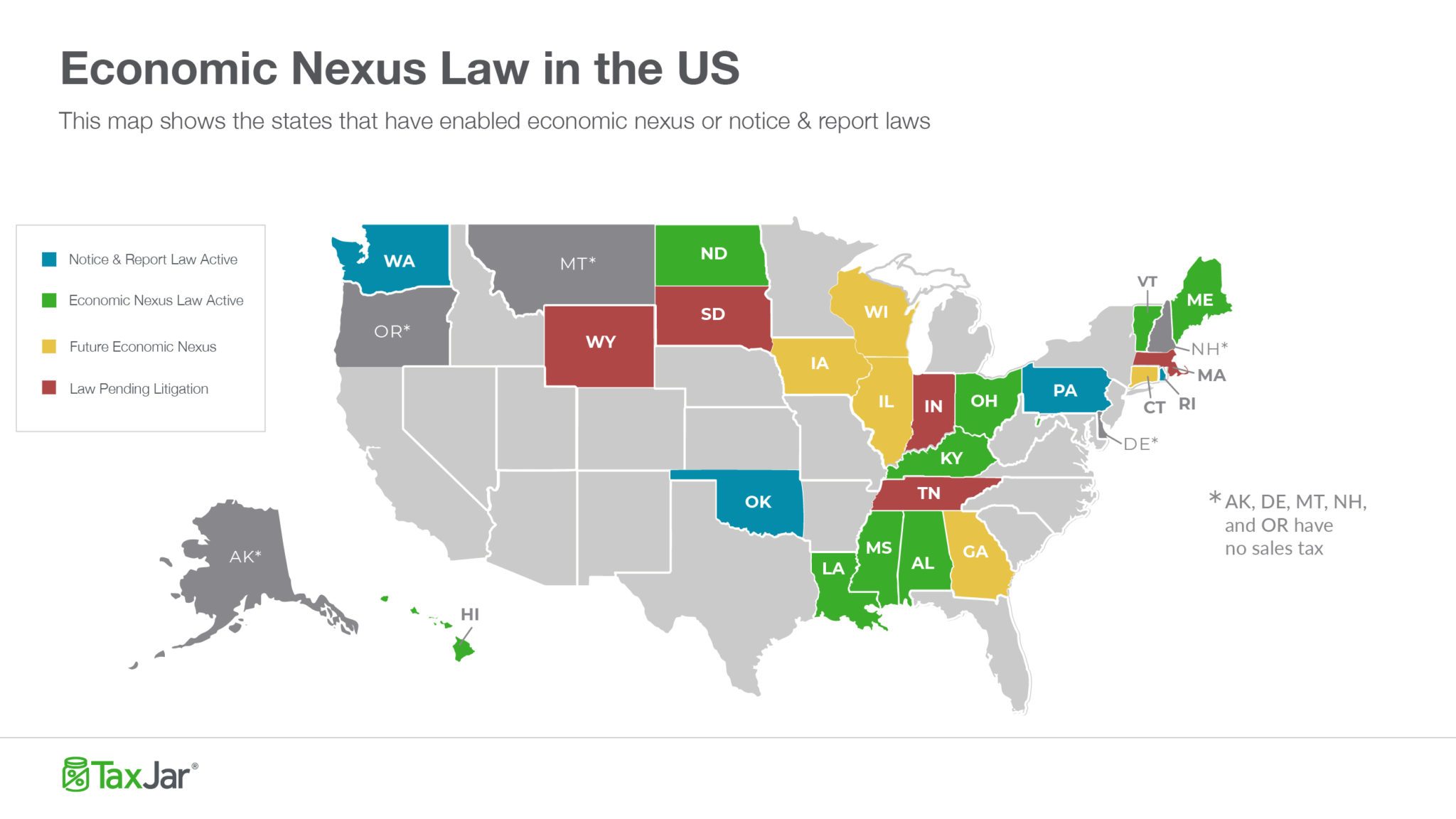
Nexus is essentially your physical influence or presence within a state. If you have “nexus” within a region, then you can be required by law to collect and pay sales taxes lest you incur fines and compounding interest. The idea is used to declare and determine where a business may have a physical presence even outside their home state.
Determining nexus has always been particularly tricky because each state varies regarding qualifications. What gives you nexus in one state may be completely different in another. And this supreme court ruling just made it even more difficult, especially for SaaS providers who operate and serve on a broad level outside of their home location(s).
As a result, South Dakota now has an economic nexus law — among 25 other states and counting — that increases the tax burdens of online businesses, SaaS and cloud service providers included. What this means is that general tax burdens will grow, and companies will need to expansively research tax burdens on a state-by-state basis with more scrutiny than ever before. This has happened before, further muddling the definition of nexus and sales tax when it comes to online services, so it’s not unreasonable to think it will be expanded even more in the future.
A major issue with these tighter laws is that they tend to have low limits: 200 total transactions — as opposed to customers outright — in a state will commonly develop nexus. But since SaaS providers deliver subscription-based pricing models and deal with multiple invoices per client, you can end up with nexus in a state faster.
This further facilitates the need to have an accountant or experienced professional deal with taxing and monetary collection policies. Don’t overlook this, especially if your business is spread across varying locations and your service coverage is far-reaching. You will need to identify and understand where sales tax is necessary, and failure to do so will lead to severe consequences not the least of which is heavy legal fines and court costs.
Provider-focused auditing
Security and data governance audits are less an optional state of checks and balances and more a legal and regulatory requirement these days. Therefore the onus has shifted to providers to help deal with and prepare for some of these experiences.
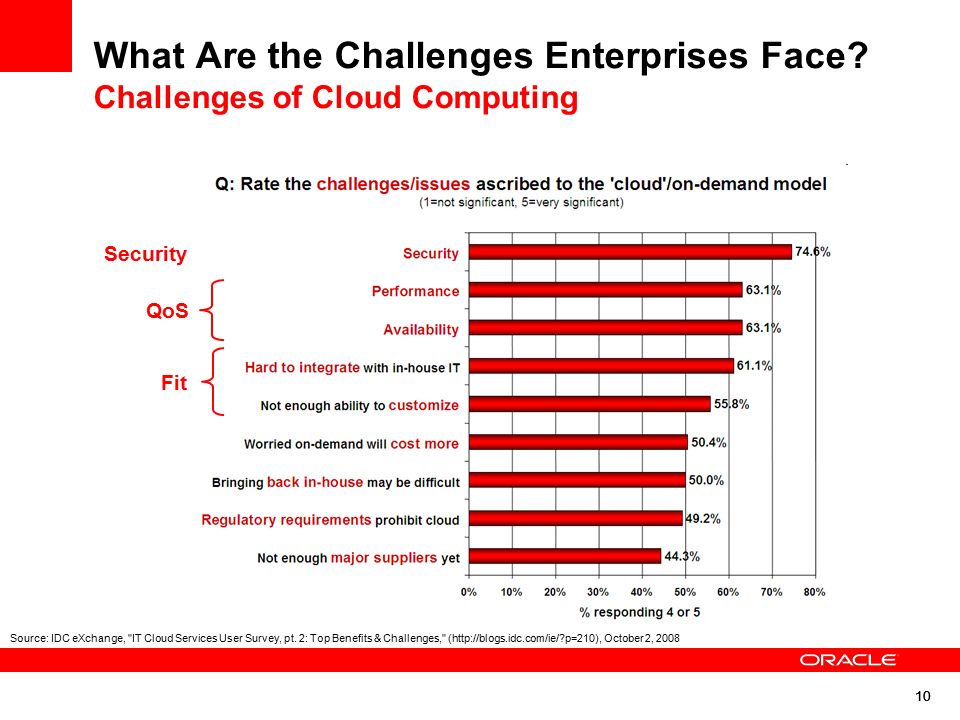
Increasingly, SaaS clients require records on IT security audits, clear-cut data storage, handling and protection policies, performance standards, end even risk management or disaster recovery plans. In other words, you may be initially audited by clients — in a way — before any legal audits take place.
Common auditing concerns
More than proper planning and documentation, it helps to have these elements established long before your clients even ask, so that when the time comes, you can provide the necessary assurances.
Here are some things to consider for future and present audits:
- Do you have a corporate security policy?
- Is there a dedicated security team in place to handle events and failures?
- Do you have a formal procedure for reporting a security violation or data breach?
- Do you regularly conduct penetration testing or have a third-party handle the process? When was the last relevant test performed, and what were the results? What are you doing to remedy any flaws or vulnerabilities discovered?
- Whether through external means or internal discovery, what are you doing to both identify and remediate vulnerabilities in your system and network?
- How often are applications or software tools updated? What is the process for doing so and how does this affect security? What about customer or client downtime? How long will the update process take?
- Do you have a process for announcing and sharing scheduled maintenance sessions?
- Is there API access or external integration support? How does this relate to data security and protections?
- Are all API units authenticated, data encrypted, and monitored?
- How do you physically secure access to your data facilities or operations sites?
- How do you comply with HIPAA/Sarbanes-Oxley/PCI DSS 3.0/ and other similar-level regulations? Do you have documentation to support this?
- Are all your processes — including data backups — documented in full with details on how you handle operations?
- How far does your disaster recovery plan extend? What will you do if your customers are affected by a breach? How will you continue to ensure their privacy and security?
Legally mandated data protections

GDPR or the General Data Protection Regulation in the European Union is designed to protect businesses from overreaching and provide more assurance for citizens in regards to personal data and privacy. For example, one new requirement from the law forces companies to offer a “forget me” option that allows European citizens to not only download and see any personal associated data collected about them but also delete it in full.
Since SaaS in the enterprise is not inherently a consumer-level business it’s easy to fall into the trap of thinking GDPR doesn’t apply. But it does, in some cases even on multiple levels. With some providers, for example, the protections may extend to customers, a customer’s customers and sometimes beyond. This means that even if your company or business doesn’t serve affected customers, but one of your clients or service users does, then you’re obligated to comply where applicable.
Under GDPR, the purpose, nature and storage duration of data must all be supplied and honored. That is, if you say you’re going to keep data for two years, then you should immediately purge it after said period. You must also define and adhere to the type of data being processed, while also considering the responsibilities, rights and requirements of customers — who generally serve as the source or inherent “owner” of specific data sets.
This extends to security protections, as well. Customers must be informed of a breach or security issues as soon as it a company is aware of it. Providers must ensure that protections are in place to prevent data breaches and fully secure customer information. Failure to do so will result in hefty fines.
Here’s a GDPR and protections checklist you can review to ensure ultimate compliance:
It’s important to understand, however, that no matter how comprehensive this checklist may seem, there’s much more that goes into ensuring compliance. Therefore, it’s crucial you do your due diligence to research and understand the new regulations and how they apply to your business and operations.
General data practices
Outside of the legal and regulatory space, there’s also the matter of protecting your data and digital assets internally.
Throughout most of your auditing and data protection strategies, you’re focused on external data channels that often stem from your customers and umbrella users. It’s easy to forget that you — as a business — have your own proprietary data and trade secrets that you need to handle properly.
Here are some questions you should be asking:
- How often do you back up your sensitive data and where is it stored?
- How often are backups completed? If there is a data breach, failure or complication what could be lost?
- What security measures do you have in place to retain control of your systems and network?
- How will service interruptions affect your customers, their data and their users?
Protecting data that belongs to your customers and clients is vital, but you need to protect the content that relates to your business or organization and its primary operations as well. If you offer a cloud-service application, for example, where is the source code housed and is it handled or edited in a way that won’t compromise the entire business?
The landscape is tumultuous; be ready to evolve
As is evident through many of the discussions in this guide, the world of cloud computing and SaaS is changing considerably, along with the rest of the enterprise market. There’s a general focus on network and user security, data protection, customer rights and moral responsibility in some cases in regards to products and service offerings. Sometimes, as is the case with GDPR, regulations extend beyond your direct clientele and stretch further down the chain to include anyone affected by internal data usage and collection.
That’s why compliance internally is crucial to the success and continued operations of your business. The last thing you need to deal with are repercussions handed down by government bodies, your customers or the community at large.







 Workflows
Workflows Projects
Projects Data Sets
Data Sets Forms
Forms Pages
Pages Automations
Automations Analytics
Analytics Apps
Apps Integrations
Integrations
 Property management
Property management
 Human resources
Human resources
 Customer management
Customer management
 Information technology
Information technology



Benjamin Brandall
Benjamin Brandall is a content marketer at Process Street.